Your Epic Guide to Website Security
13 of Our Most Epic Posts on Website Security, Data Breaches, Cyber Attacks and How Not to Be a Hacking Victim
(Scroll down for all stories below, or just click on the links.)
How Website Security Can Boost Your Sales and Lower Your Bounce Rate (Video)
4 Security Risks To Your Ecommerce Site and How to Fix Them
Why We Love “How hacking hurts your website’s ranking in search results”: Article Review
Cyber Security Predictions for 2016
6 Key Security Terms Every Business Owner Should Know
Wireless Mice and Keyboards Latest Tools in Hackers’ Arsenal: Report
The Biggest Threat To Your Ecommerce Business: New Report
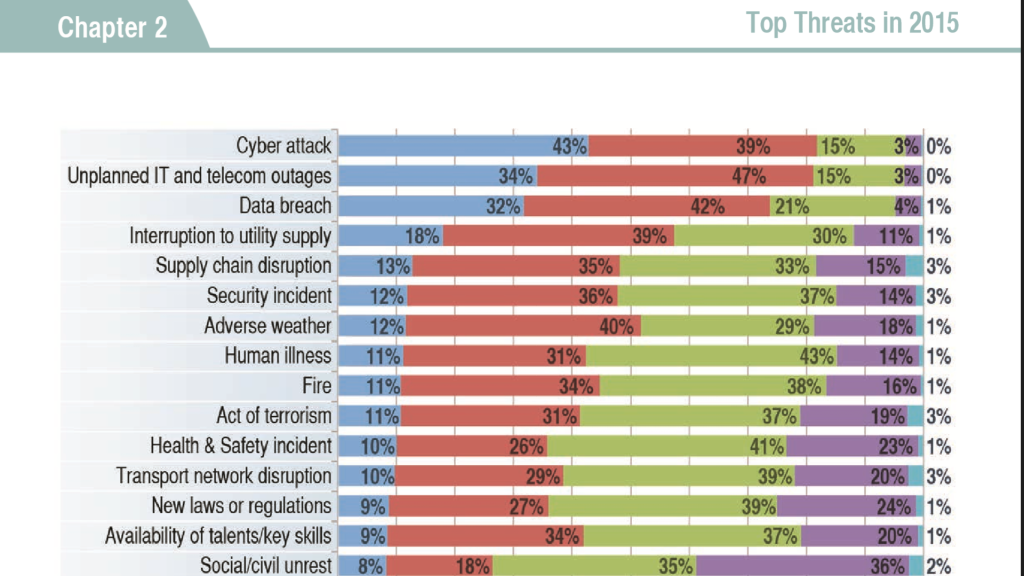
The Top Cyber Attacks and Data Breaches of 2015
3 Must-Watch Ted Talks on Cyber Security (Video)
3 Takeaways From the TalkTalk Data Breach
Report: 1 in 3 Patient Healthcare Records Will Be Hacked in 2016
14 Unexpected Things You Didn’t Know Could Be Hacked
Nearly Half of All Businesses Hit By Costly Data Breaches: Report
4 Security Risks To Your Ecommerce Site and How to Fix Them
Alarming newspaper and industry reports show that no one, including small businesses, is immune from a potential data security breach. According to a 2013 survey by National Small Business Association, half of all small businesses surveyed had been a victim of a cyber attack.
The best way to protect yourself is with a comprehensive security protection plan and knowing some of the tricks hackers use that can cost you time, money and spur mistrust from your customers. Here are four risks that could make you a target for hackers – and how you can fix them.
Risk: Weak passwords
The necessity of a strong password is so basic it should be a no-brainer, right? But a strong password is one of your first lines of defense against unscrupulous hackers, so it bears a mention.
Fast Fact: Studies have shown that website users typically have only one password for multiple accounts, leaving customer information and business data vulnerable to hacking.
What you can do: Experts recommend you create a password that’s at least eight characters long, with a combination of capital letters and symbols. And it’s better if passwords aren’t real words, either, which makes them easier to hack. Create a password that’s gobbledygook (that you can remember) rather than a real word and you’re more likely to evade hackers.
Risk: Phishing
We’ve all gotten those emails: an African prince needs us to transfer him money, etc., etc. Some attempts to steal our data and get our money are so blatant it’s almost laughable. But there are more subtle phishing techniques out there, that, if you’re not vigilant, could be as simple as one unaware-click away to open the door to a hacking maelstrom. Phishing can come in the form of a legitimate-looking email with an attachment or link to a virus, malware or spyware.
Fast Fact: Phishing attacks have been steadily rising each year, according to the Anti-Phishing Working Group, which works to create a unified global response to cyber crimes.
What you can do: Don’t click without thinking first. Copy and paste a link to a URL rather than clicking on it. Keep your operating system and software up to date.
Risk: Untrained staff
You can have an exemplar internet security plan in place, but have your employees been trained on how not to let an intruder in through the gates? Employees not trained on cyber security methods is like having staff who don’t know how to set the code for the alarm system.
Fast Fact: Nearly 19 percent of Americans surveyed said they had never changed their PIN or password without first being prompted, according to a survey conducted by The National Cyber Security Alliance and PayPal.
What you can do: The National Cyber Security Alliance, a nonprofit focused on internet safety, recommends training employees to create strong passwords, to back up their work and how to spot and not click on suspicious links and attachments in emails.
Risk: Social engineering
Instead of tediously trying to hack into software, hackers try to get information directly from the source: you. They may try to get you or an employee to install malicious software or use you to gain access to unauthorized locations.
Social engineering is one of the latest tactics hackers use and is on the rise, according to a January 2014 recent article from Inc. Magazine.
Fast Fact: The average cost to a small business that’s been hit by a cyber attack was more than $9,000, according to a 2013 National Small Business Association survey.
What you can do: Be careful of what personal information you reveal online. Beware of hackers pretending to be from your company’s IT department and asking for sensitive data or passwords.
Cyber Security Predictions for 2016
From headline-making news like the data breaches at Sony and Ashley Madison this year, to the OPM and persistent threats of cyber terrorism from countries like China and South Korea come predictions for what’s in store for cyber security in 2016. Experts largely agree that mobile devices face bigger risks, the stakes for political hacking attacks are high and data breaches are going to get much worse and even more prevalent.
We’ve gathered below some early predictions from website security experts for what’s in store for next year. Among the predictions are:
1. Attacks on mobile devices are going to increase.
2. Ransomware is on the rise.
3. The Internet of Things (IoT) makes every day life vulnerable to hacking.
4. Cyber attacks will be more sophisticated and harder to detect and trace.
With cyber crime on the rise, every business is vulnerable to attack. Keep your ecommerce site protected with website security from Trust Guard.
Information Age: Top 6 cyber security predictions for 2016
PC Tech: Top 10 CyberSecurity predictions for 2016
News.com.au: Intel Security’s 2016 Threat Prediction report
ZDNet: Security in 2016: The death of advanced persistent threats
Remember, despite the saying, forewarned does not mean forearmed. Arm yourself with website security designed to keep ecommerce sites just like yours safe from hackers. Learn more at trust-guard.com.
6 Key Security Terms Every Business Owner Should Know
If you’re a business owner trying to make sure your website is safe, secure and trustworthy to customers, navigating your way through the dizzying array of cyber security-related can be confusing, frustrating and just plain boring. We’ve put together this in-a-nutshell guide to make it as painless and simple for you to understand some key security terms so you know what your site needs and why.
Trust Seal
What it is: Trust Seals are graphics for your website’s homepage that show customers your site is safe and secure and that you are who you say you are. There are many companies that offer various kinds of trust seals. The three main types are Privacy Seals, which lets customers know their personal and financial information is safe; Business Seals, which show that an outside company has verified that you are who you say you are; and Security Seals, which demonstrate that your site has been scanned for viruses and security holes.
Why you need it: More customers, more sales, more ka-ching! Trust seals have been shown to increase consumer confidence, decrease shopping cart abandonment and boost sales. When customers feel your site is secure, they’re more likely to buy from you.
Privacy Policy
What it is: A privacy policy lets visitors know what information you collect from them and what you do with it. In legal terms, a privacy policy is a disclosure document. There are state and federal laws governing internet privacy and the FTC and state attorney generals have jurisdiction in enforcing those laws.
Why you need it: A comprehensive, specific privacy policy tailored for your site can help protect you against complaints and potential lawsuits. Facebook and Google have each faced lawsuit connected to their privacy policies and use of user data. But be aware that simply copying and pasting an existing privacy policy from another company’s website simply won’t do: you need one that matches the specific ways in which your company gathers and uses visitor information. Many companies, such as Trustee and FreePrivacyPolicy.com, offer services to create privacy policies for your site in minutes.
SSL Certificate
What it is: An SSL (it stands for Secure Sockets Layer, if you really want to know) Certificate is a digital form issued by an outside party that says your site is authentic and uses SSL encryption to scramble data from a customer’s computer to your server so their info is protected from third parties trying to access it. SSL certificates include the certificate holder’s name, the certificate’s serial number and expiration date, a copy of the certificate holder’s public key, and the digital signature of the certificate-issuing authority.
Why you need it: If your company takes online payments or collects sensitive information, you need it. An SSL certificate is an added layer of protection to help assure your customers that your website is safe. It won’t protect you (or them) from hackers, but when visitors see the padlock in the browser window that indicates that SSL encryption is being used, it can help build confidence that your company is taking steps to protect their data.
PCI Compliance
What it is: Payment Card Industry Compliance applies to you your company collects, transmits, processes or stores cardholder information. Being PCI Compliant means you’re following industry requirements to keep your customers’ data safe. The regulations were developed by a council (Payment Card Industry Security Standards Council – aka PCI SSC) set up by the big credit card companies – Mastercard, Visa, American Express, Discover and JCB.
Why you need it: Do you want to pay massive fines? Didn’t think so. If you’re not PCI Compliant, then you’ve got to pay up. The regulations are too complex to get into in a brief summary, but here’s a detailed explanation.
Vulnerability Scan
What it is: Vulnerability Scans check for security holes in computer networks to make sure you’re not letting the bad guys in. They typically are automated scans and should be run continuously.
Why you need it: You don’t want hackers stealing your info, causing your customers to distrust you and costing you money, do you? Of course not! Vulnerability Scans help protect your network and your customers’ data and are the first step toward being PCI Compliant and getting a Trust Seal (we mention both above.) For more deats on vulnerability scans, we’ve got it covered here.
IT Penetration Test (PenTest)
What it is: PenTests actively, intentionally attack and exploit a computer system to see if there are any holes in your network. It’s basically like a hacker attacking your network, only they’re on your side. PenTests require expertise and aren’t automated like vulnerability scans are.
Why you need it: Combined with vulnerability scanning, Pen Tests give you comprehensive security coverage. PenTests should be done once a year by a computer security expert (or good guy hacker, if you will) to identify what data was compromised during the test. Need more on Penetration Testing? You can find it here.
Wireless Mice and Keyboards Latest Tools in Hackers’ Arsenal: Report
A new tool has emerged in hackers’ toolboxes that allows them to access computers through a user’s wireless mouse or keyboard. This hacking method, referred to as “mousejacking” by internet of things research firm Bastille, was revealed in a new report issued by the organization.
According to a recent article from Wired, “With about fifteen lines of code, you can take over a computer more than a hundred yards away.”
Usually wireless keyboards use encryption, but mice don’t always use encrypted signals.
Through their security research, Bastille discovered that “you can send out a wireless signal that pretends to be a wireless mouse… Then, you can have that fake wireless mouse pretend to be a wireless keyboard — and start controlling someone else’s computer, ” according to an article from CNET.com.
Bastille theorizes that since so many of these wireless devices use the same wireless chip, there could be millions affected by this security flaw.
CNET has compiled a list devices Bastille has found so far to be affected. You can check out the list of affected devices here to see if you have a wireless mouse or keyboard that might make you prey to hackers.
This latest discovery of a security flaw that could afflict millions of devices and users is yet another example of how essential website security is for your ecommerce site.
If you’re looking for top-notch, cost-effective website protection, then Trust Guard has what you’re looking for. Check out trust-guard.com for quick, comprehensive cyber security from a global leader in keeping sites like yours safe and protected. Start your free 14-day trial today.
3 Must-Watch Ted Talks on Cyber Security (Video)
If your ecommerce site doesn’t have internet security measures in place, it’s the same as leaving the front door open to a brick-and-mortar store. The thieves will just waltz right in, taking whatever they want: your customer’s credit card info, their passwords, and your hard-earned cash.
So any smart ecommerce business owner knows that internet security is a necessity, not an afterthought. These three Ted Talks on cyber security from experts in the industry highlight how everyone is a potential victim of cyber crime and show some things you can do to fight back.
Everyday Cybercrime – And What You Can Do About It
Speaker James Lyne shows how commonplace actions people take online without much thought are often what lead to data theft.
The 1s and 0s Behind Cyber Warfare
Cybersecurity researcher Chris Domas tells of how researchers study patterns to unlock binary codes used in cyber attacks.
What’s Wrong With Your Password?
Speaker Lorrie Faith Cranor analyzed thousands of passwords to learn the common mistakes that users make which threaten their online security.
Need a cost-effective way to easily secure your site, your data and your money? Trust Guard can help. Visit trust-guard.com for more info.
The Biggest Threat To Your Ecommerce Business: New Report
In a new survey, organizations around the globe say cyber attacks and data breaches are the biggest threat to their business.
760 small and medium businesses based in 72 countries worldwide were surveyed in The 2015 BCI Horizon Scan Survey’s annual report.
82% of respondents said cyber attacks were their number one concern, with data breaches taking first place for almost three-quarters of those surveyed.
The alarm over cyber attacks and data breaches has steadily risen over the past three years, ranking third in 2013, then moving to second place in 2014 until it claimed first place in 2015.
According to the report,
Cyber threats are now seen as the top threat to businesses worldwide with 82% of participants stating that they are either ‘extremely concerned’ or ‘concerned’ about this.
The report said that the growing concern over cyber attacks “may be attributed to recent cyber attacks on organisations like Sony and the emergence of state actors perpetrating these attacks.”
Adding to the anxiety over cyber attacks is the rising cost of such attacks. The report references a 2014 Ponemon Institute study that estimates that the average annual cost of cyber attacks worldwide is an astonishing $7.6 million. That’s an increase of more than 10% from the previous year. Data breaches are costing businesses an average of $5.9 million, up from $5.4 million the year before, according to another study from the Ponemon Institute.
So if the threat of a cyber attack or data breach wasn’t already on your radar, it should be. And if you aren’t taking every precaution against cyber threats with a website security protection plan, you should be. It’s easy to get hacked, but fortunately, it’s even easier to get protected.
Trust Guard has a proven track record in successfully protecting ecommerce businesses just like yours. It’s quick and easy to sign up. Why not give yourself some peace of mind and check out one of the global in website security? Visit trust-guard.com for more info.
Report: 1 in 3 Patient Healthcare Records Will Be Hacked in 2016
Although CBS News christened 2014 “The Year of the Data Breach,” (arguably prematurely) cyber attacks are predicted to only increase in frequency and breadth in 2016. No industry will be immune, including healthcare, which saw 100 million records hacked in 2015, according to a recent report from IBM.
Now a new report predicts that an incredible 1 in 3 patient records will be comprised in 2016.
Such dire predictions aren’t limited to healthcare, of course, but include ecommerce businesses and pretty much every entity that has any kind of online presence. It’s a reminder that an essential part of ecommerce is protecting what you’ve worked so hard to build.
Below is the full article from Computerworld which details the report.
Computerworld: Cyberattacks will compromise 1-in-3 healthcare records next year
Related: Cyber Security Predictions for 2016