Check Out Our Most Popular Posts
-
Why Multitasking Is a Waste of Time
15 Jan, 2018
-
Is Your Company Staying Competitive?
13 Dec, 2017
-
Grinch-Like Hackers Could Ruin Your Christmas Cheer
12 Dec, 2017
-
Overcoming Price Issues In Your Niche
27 Nov, 2017
-
Online Christmas Shopping Fears
1 Nov, 2017
-
5 Reasons Why Your E-commerce Business May Fail
25 Oct, 2017
-
18 Sep, 2017
-
Show You Care About People’s Privacy
13 Sep, 2017
- 4x Buyer Protection Blog blogging Business Business and Economy Credit card Customer service Cyber Monday cyber security Data breach E-commerce Ecommerce Facebook Google hackers hacking Identity theft increase conversion increase conversion rates increase sales increase sales conversion Increase Traffic Internet Marketing Kissmetrics live chat marketing Marketing and Advertising online business Online shopping Payment Card Industry Data Security Standard pci compliance Point of sale practical ecommerce privacy policy Rhino Support Live Chat Search engine optimization Security Small Business social media Social media marketing target security breach Trust Guard trust seals Twitter website security
Categories
- 2016 cyber security predictions
- 4x Buyer Protection
- App Developers
- best ecommerce sites
- Black Friday
- Black Friday 2015
- Blogging
- Building Trust & Strong Customer Relationships
- business
- Conversion Rates
- conversions
- Customer Service
- cyber attack
- Cyber Monday
- Cyber Monday 2015
- cyber security news
- data breach
- eCommerce
- ecommerce news
- ecommerce site design
- EMV
- explainer videos
- Facebook ecommerce
- Facebook shopping
- Halloween
- Holiday 2015
- Holiday shopping
- identity theft protection
- Improving Site Traffic
- Increase Sales
- Keyword Research
- Little Tips That Make A Big Difference
- live chat
- Marketing
- Mobile Commerce
- Mobile Security
- PCI Compliance
- PCI Scanning
- Podcasts
- POS System Protection
- Price Matching
- privacy policy
- Ratings and reviews
- Rhino Support
- search results
- SEO
- shipping insurance
- Shopper Approved
- Shopping Apps
- social media
- Social Media Campaigns
- Tech And Business News
- Ted Talks
- Terms of Service
- terms of service generator
- top ecommerce sites
- ToS
- Trust Guard
- Trust Seals
- Trust Seals
- Uncategorized
- Valentine's Day 2016
- Website Security
- Website Security And 3rd Party Verification
NEWS
-
Instagram’s Successful E-Commerce Model
31 Mar, 2017
-
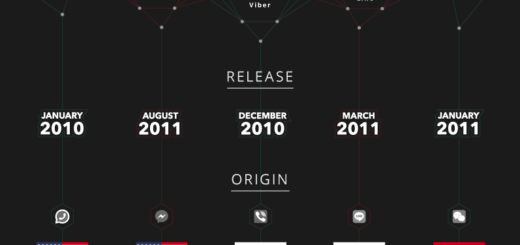
Which Messaging App Do You Use?
1 Mar, 2017
-
Walmart May Invest in E-Commerce Giant Flipkart
3 Oct, 2016
-
What Ecommerce Merchants Need to Know About EMV
1 Jul, 2016
More
Search
Website Security
-
The UK Is Taking Online Security More Seriously
31 Oct, 2016
-
After Hack, Yahoo! Offers Online Security Tips
28 Sep, 2016
-
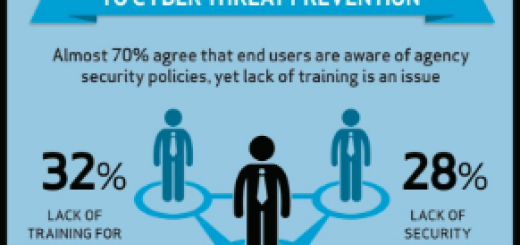
Do You Offer Security Awareness Training?
14 Sep, 2016
eCommerce
-
Why Multitasking Is a Waste of Time
15 Jan, 2018
-
Is Your Company Staying Competitive?
13 Dec, 2017
-
Grinch-Like Hackers Could Ruin Your Christmas Cheer
12 Dec, 2017
-
Overcoming Price Issues In Your Niche
27 Nov, 2017
-
Online Christmas Shopping Fears
1 Nov, 2017
Recent Posts
- PCI Compliance: What You Need to Know to Protect Your Business June 5, 2018
- Why Multitasking Is a Waste of Time January 15, 2018
- Is Your Company Staying Competitive? December 13, 2017
- Grinch-Like Hackers Could Ruin Your Christmas Cheer December 12, 2017
- Overcoming Price Issues In Your Niche November 27, 2017